Microsoft uncovers ‘Dirty Stream’ attack, a major Android vulnerability.
In a recent revelation, Microsoft has uncovered a pervasive vulnerability pattern in multiple widely-used Android applications, potentially affecting billions of users worldwide. Termed the “Dirty Stream” attack, this vulnerability could lead to arbitrary code execution and token theft, posing significant security risks to Android users.
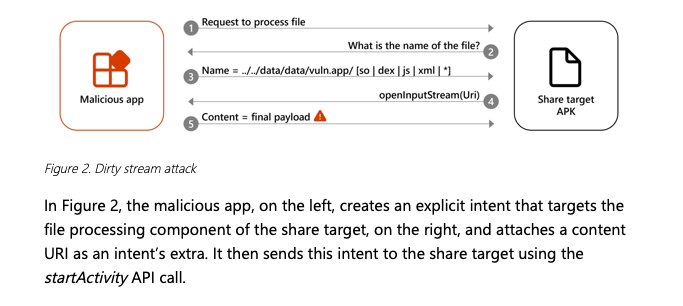
According to Microsoft Threat Intelligence, the vulnerability stems from a path traversal-affiliated flaw, enabling malicious apps to overwrite files in the targeted app’s home directory. This exploit grants threat actors full control over app behavior and access to sensitive user data.
The implications are alarming, with over four billion installations of vulnerable apps identified in the Google Play Store. Microsoft urges developers to conduct thorough checks on their apps, implement necessary fixes, and bolster security measures to prevent future vulnerabilities.
As part of responsible disclosure practices, Microsoft collaborated with app developers like Xiaomi, Inc. and WPS Office to address the issue promptly. Fixes have been deployed, but users are advised to keep their devices and apps updated.
The collaboration extended to Google, with Microsoft and the Android Application Security Research team publishing guidance for developers to avoid similar vulnerabilities. Recommendations include rigorous validation of file-sharing mechanisms and adoption of robust security protocols.
The “Dirty Stream” attack underscores the critical need for proactive security measures in the ever-evolving threat landscape of mobile applications. With threats becoming increasingly sophisticated, industry collaboration and vigilance are paramount to safeguarding user data and privacy.
Sources:
Full article on Microsoft Threat Intelligence: “Dirty stream” attack: Discovering and mitigating a common vulnerability pattern in Android apps.
Android Developer: Improperly trusting ContentProvider-provided filename





 0
0



